The Ultimate Guide to Huntress EDR and Veroot Partnership for IT Providers
Veroot is a proud partner with Huntress EDR! We have complete confidence in their ability to diligently monitor our systems and collaborate with...

Achieving ISO 27001:2022 certification is a significant milestone for any company, particularly for those in the compliance software industry. For our company, this certification underscores our commitment to robust information security management, protecting sensitive data, and fostering trust with our clients. Here, we share insights from our journey to certification and how it continues to shape our operations.
ISO 27001:2022 is the latest version of the Information Security Management System (ISMS) standard. It emphasizes risk management, continuous improvement, and aligning information security strategies with business objectives. Key components we implemented include:
Establishing an ISMS tailored to our business needs.
Conducting comprehensive risk assessments and implementing necessary controls.
Regularly monitoring and reviewing the effectiveness of our security controls.
Ensuring compliance with legal, regulatory, and contractual obligations.
From the outset, securing executive-level support was crucial. Leadership recognized that achieving ISO 27001:2022 certification would:
Enhance client trust and strengthen our competitive edge.
Improve our risk management strategies and ensure legal compliance.
Protect against data breaches and preserve our reputation.
This backing ensured the allocation of resources and fostered a culture of security across the organization.
Our journey began with a thorough evaluation of our existing practices against ISO 27001:2022 standards. This gap analysis identified areas needing improvement, including:
Updating documentation and policies.
Strengthening our technology infrastructure.
Enhancing employee awareness through targeted training programs.
We used this analysis to develop an actionable plan, addressing each gap systematically.
We assembled a cross-functional team with representatives from IT, HR, legal, operations, and customer support. This team was responsible for:
Defining the scope of our ISMS.
Implementing and maintaining security controls.
Ensuring compliance across all departments.
Their collaboration ensured the ISMS became an integral part of our daily operations.
We clearly defined our ISMS scope, aligning it with our business processes, information assets, and geographical reach. This scope reflects our commitment to protecting client data and supporting operational excellence.
ISO 27001:2022 requires extensive documentation and effective controls. Key measures included:
Establishing robust information security policies.
Creating a risk treatment plan to address identified vulnerabilities.
Implementing stringent access control measures to safeguard sensitive data.
We also leveraged Annex A of ISO 27001:2022, integrating its controls into our organizational framework.
Our employees play a critical role in maintaining information security. Regular training sessions and workshops have ensured:
Awareness of security policies and procedures.
A clear understanding of individual roles in safeguarding data.
Prompt recognition and reporting of potential security threats.
Regular internal audits have been pivotal in maintaining our ISMS. These audits:
Identified areas for improvement.
Ensured readiness for external audits.
Reinforced our commitment to continuous improvement.
We partnered with an accredited certification body experienced in ISO 27001:2022 and compliance software. Their expertise ensured a smooth certification process, which included:
A thorough review of our documentation and ISMS readiness.
A comprehensive evaluation of the implementation and effectiveness of our controls.
Achieving certification was just the beginning. To maintain compliance, we:
Conduct regular surveillance audits.
Monitor and improve our ISMS continuously.
Stay vigilant against evolving security threats and adopt best practices.
Maintaining ISO 27001:2022 certification requires ongoing collaboration between our ISMS team, development team, and customer support staff. Development teams have integrated secure coding practices into our software development lifecycle (SDLC).
Their close collaboration with the ISMS team ensures vulnerabilities identified during risk assessments and penetration testing are promptly addressed.
Customer support staff play a vital role in protecting client data. They receive regular training to understand data handling policies and incident response procedures.
Their proactive reporting of anomalies or potential breaches is crucial to our security framework. Joint exercises and workshops across teams have strengthened interdepartmental communication and unified our approach to compliance.
Our ISO 27001:2022 certification journey has been transformative. It has reinforced our commitment to information security, elevated client trust, and enhanced operational efficiency.
The certification is more than a badge of honor; it is a testament to the collaboration, dedication, and continuous improvement embedded in our company culture. By fostering coordination across teams and prioritizing information security, we continue to uphold the highest standards of compliance and excellence.
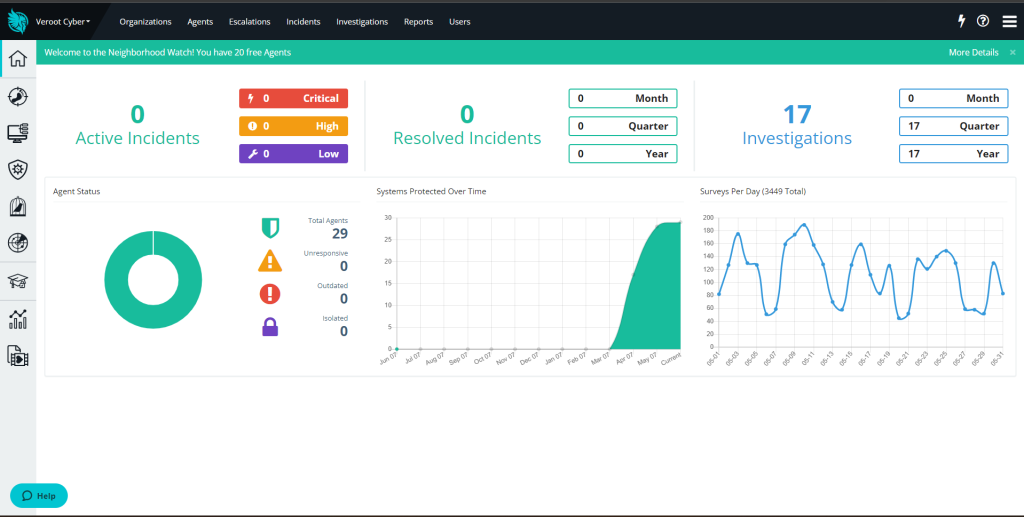
Veroot is a proud partner with Huntress EDR! We have complete confidence in their ability to diligently monitor our systems and collaborate with...
 Read More
Read More
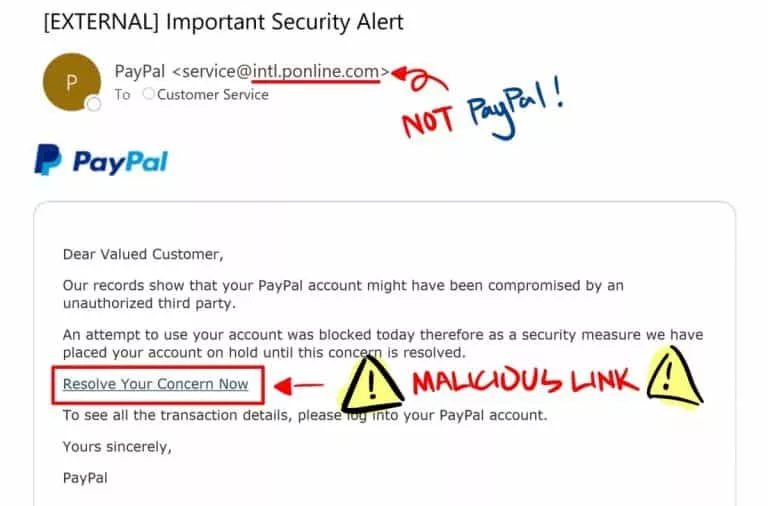
Phishing and Spoofing are two of the most prevalent types of cyber-attacks used by malicious actors against businesses and organizations today.