Russian Hacker Group ‘Star Blizzard’ Upgrades Phishing Stealth, Research Uncovers
State Sponsored Villains “Star Blizzard” (aka Seaborgium, BlueCharlie, Callisto Group, Coldriver) has been actively involved in cyber espionage since...
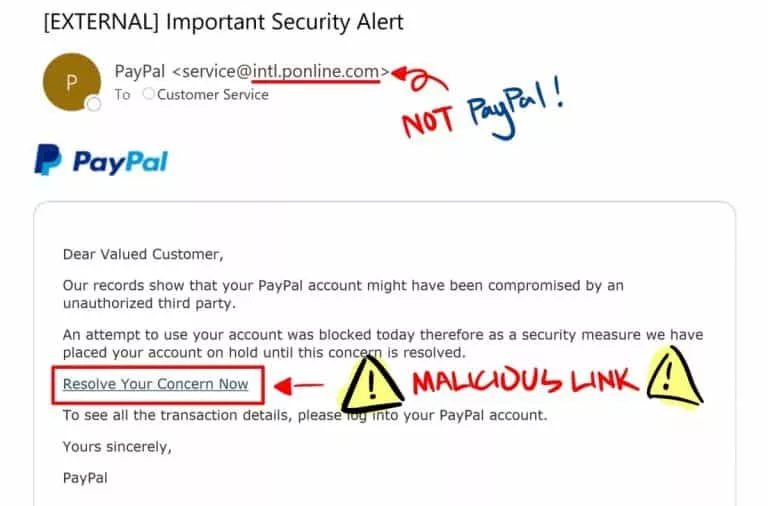
Spoofing involves impersonating legitimate email users, which can be accomplished through a Google search for basic information. It is crucial to exercise caution and carefully scrutinize the contents of all emails received.
Although a message may appear to be from a known sender, further investigation may reveal that the email was sent by a fraudster.
Below is what to do when you encounter an email:
It is important to remain vigilant and emphasize the importance of ongoing education and awareness among team members to detect and prevent these types of attacks.

State Sponsored Villains “Star Blizzard” (aka Seaborgium, BlueCharlie, Callisto Group, Coldriver) has been actively involved in cyber espionage since...

Cyber Incident Response Reporting Catalogue and report the breach.

A critical security issue has been found in all versions of Exim mail transfer agent (MTA) software. This vulnerability could allow unauthorized...