2 min read
Veroot Cyber Partner - Huntress MDR/ITDR Services in Action
Ryan Kessler
:
Feb 20, 2025 1:40:52 PM

Limiting the Blast Radius of Successful Phishing Attempt
Your Cyber Team here at Veroot will be walking through a specific example of how phishing works, and how we were able to save our client enterprise wide exposure through our partner Huntress ITDR services. This example highlights the critical steps of the attack, illustrating how the phishing email was received, interacted with, and led to credential compromise. Understanding this incident helps us identify vulnerabilities and strengthen our defenses against future threats.
Description: A user received an email appearing to be from a trusted source (e.g., IT support, a bank, or a well-known company). The email contained relevant information to prompt action.
Example:
- Subject: "******* shared "NEW PROJECT PROPOSAL" with you"
- Message: "This email is generated through (Company Name) use of Microsoft 365 and may contain content that is controlled by Company Name "
- Attachment or Link: "[New Project Proposal]"
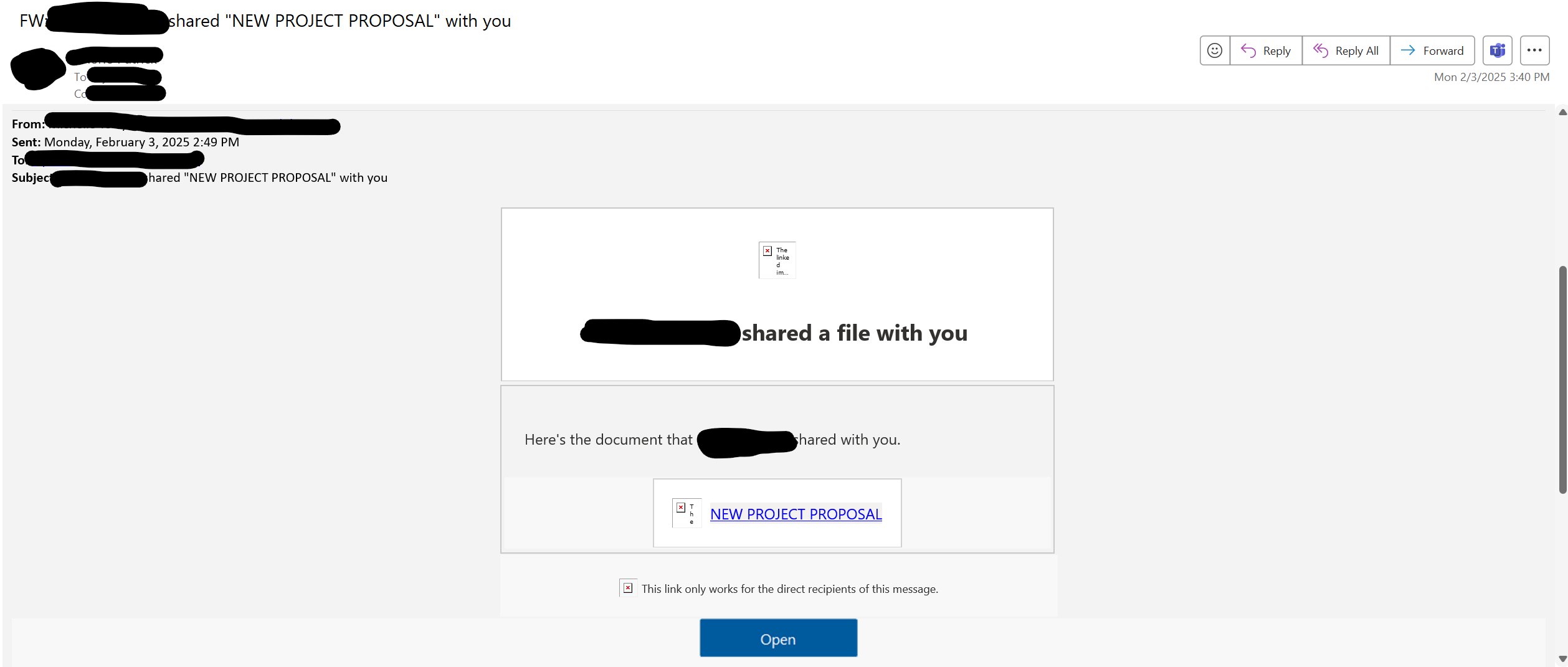
Step 2: Clicking the Malicious Link
Description: The user clicked the link in the email, which redirected them to a fake login page mimicking a legitimate website
The landing page as you can see has been professionally made.
Indicators of Phishing:
- Slight variations in the URL (e.g., "micr0soft.com" instead of "microsoft.com" “companydomain1”).
- Copyright Date – 2017
- OneDrive will not ask for log-in information to view material, unless it is restricted, or if it is enforced for your organization to do so to access shared content.
- Please ask IT/Cyber Team if these requests are legitimate.
Default answer is NO to any credential sharing.
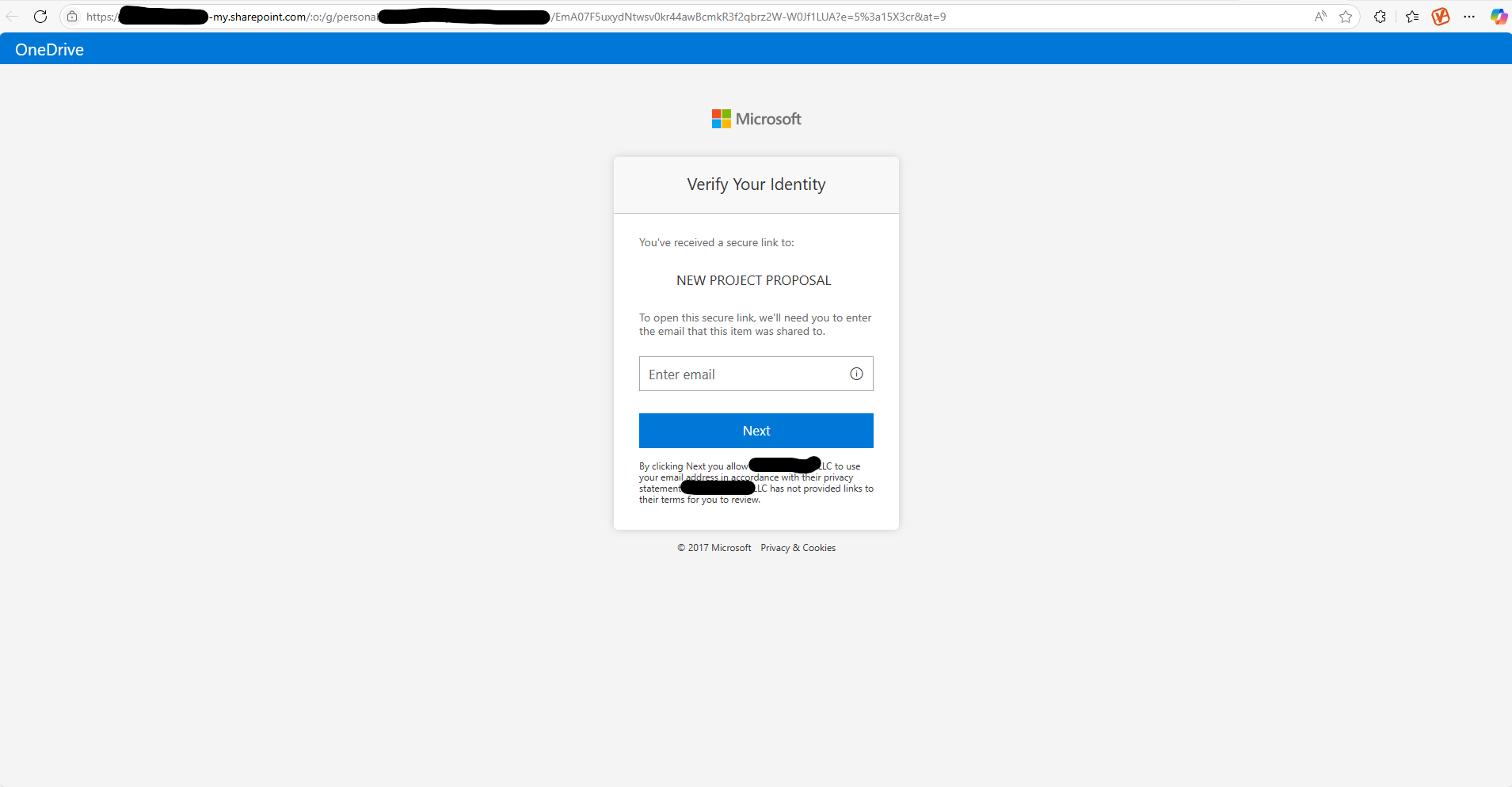
Step 3: Credential Theft
Description: The user entered their login credentials, unknowingly sending them to the attacker.
Red Flags:
- Redacted – there was a 1 added to the end of the company name included in the URL.
- Once login button was initiated the page freezes in a loop.
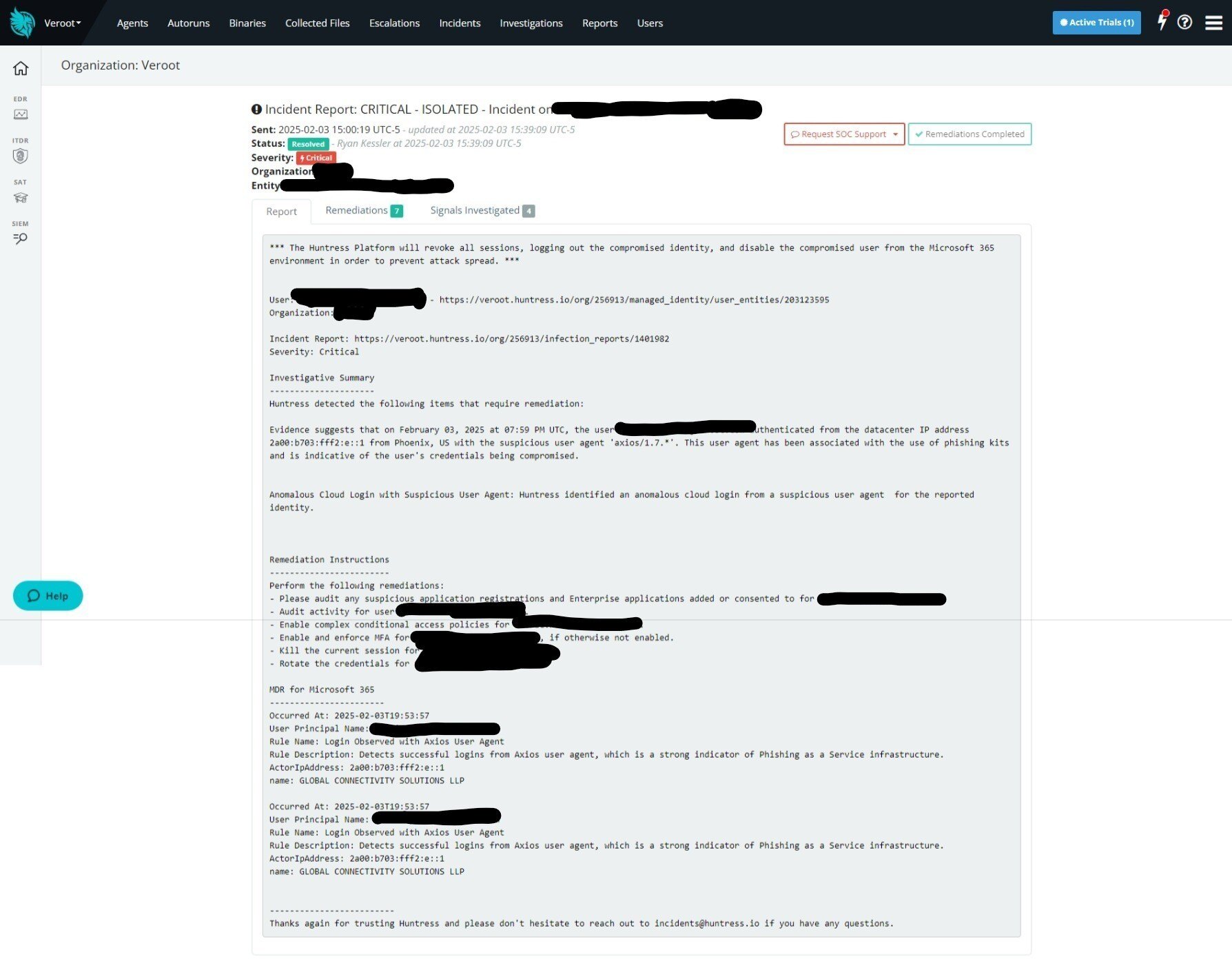
Step 4: Attacker Gains Access
Description: The attacker now has the victim’s login details and can access their account, leading to data breaches or financial fraud.
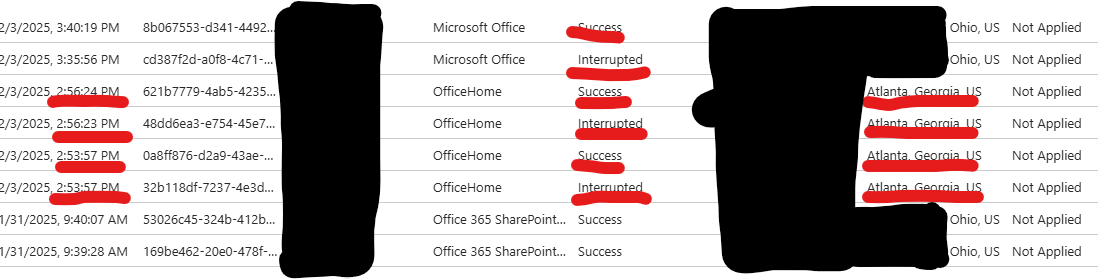
- As we can see by Geo-Location that logins have been accepted in abnormal locations.
Consequences:
- Unauthorized access to email or company accounts.
- Use of stolen credentials for further attacks. – Huntress MDR/ITDR Services was able to block access and isolate account and endpoint.
- Huntress ITDR was triggered by Geo-Location ID of login to user account.
-
Huntress continuously monitors Microsoft 365 authentication events. When a login occurs from a previously unseen geolocation (e.g., a different country or an unexpected region), ITDR assesses the event based on:
- User behavior history: Has this user logged in from this location before?
- As shown above, Geo-Location had changed from Ohio to Atlanta, Georgia.
- IP reputation: Is the IP associated with VPNs, proxies, or known threat actors?
- Huntress Detected a known User Agent - Axios, that has been used in successful phishing campaigns in the wild.
- Anomalous patterns: Does this login differ significantly from the user's normal activity?
- These detections can be confirmed through Admin portal in M365.
- User behavior history: Has this user logged in from this location before?
- The Report is shown above to Administrator(s) of Huntress account, as well as remediation steps needed to take moving forward.
Step 5: Mitigation & Response
Actions to Take if You Suspect Phishing:
- Do not click links or download attachments from unknown sources.
- Verify the sender by contacting them through official channels.
- Report the phishing email to IT/security teams
4. Reset your password immediately if credentials were entered.
5. Enable multi-factor authentication (MFA) for added security.
Why Huntress ITDR?
-
Huntress IDTR (Identity Threat Detection & Response) provides continuous monitoring to detect identity-based threats, such as compromised credentials and lateral movement, before they can escalate into full-scale breaches.
-
It enhances visibility into identity-related attack paths, helping organizations detect and respond to adversary activity within Microsoft 365, Active Directory, and other identity ecosystems.
-
Huntress IDTR reduces dwell time by rapidly detecting suspicious authentication attempts, privilege escalations, and unauthorized access, allowing security teams to take immediate action.
-
It integrates seamlessly with existing security tools, providing enriched threat intelligence and actionable insights to improve incident response capabilities.
-
By leveraging expert threat hunting and automated detection, Huntress IDTR helps small and mid-sized businesses (SMBs) strengthen their defenses against sophisticated cyber threats.
-
With a focus on post-exploitation detection and response, Huntress IDTR ensures that identity-related attacks are identified even when traditional endpoint security solutions fail to catch them.


If your business is lacking adequate M365 and EDR protections against an ever-growing threat. Please contact us at cyber@veroot.com.
Related posts you may be interested in reading:

Ransomware, How Hackers Hold Your Files Against You.
What is Ransomware?

Detecting Compromised Emails with Huntress MDR for Microsoft 365: Enhancing Cybersecurity
In the ever-evolving landscape of cybersecurity threats, email remains one of the most common vectors for attacks. Cybercriminals continuously refine...


