CTPAT Minimum Security Requirements for Importers: Corporate Security
In 2019, U.S. Customs and Border Protection (CBP) updated its minimum security criteria (MSC) to address changes to the global supply chain and the...
3 min read
Admin : Dec 7, 2023 1:00:00 PM
Whether you’re new to CTPAT certification or are preparing for validation or recertification, the U.S. Customs and Border Protection’s (CBP) minimum security criteria (MSC) will be imperative to your success. Our three-part blog series covers the first focus area of the MSC, corporate security. For an overview, read our first post. In today’s post, we’re diving into risk assessment and the third post will cover business partners.
Since the CTPAT certification was created to mitigate the threat of terrorist groups and criminal organizations, having a risk assessment that identifies these vulnerabilities is an obvious part of the MSC. Understanding exactly how to document this assessment and mitigate/eliminate necessary risks may not be as obvious to foreign manufacturers seeking CTPAT certification. Veroot is here to support you on your quest to become CTPAT-certified. Our CTPAT consultancy solutions ensure you meet the MSC — so if you’re confused about the requirements of the risk assessment or just need a partner to guide you, we’re here to help.
Multiple steps must be taken to prepare a successful risk assessment. First is a self-assessment of your supply chain practices, procedures, and policies. The purpose is to identify any threats, determine their level of risk, and then put an action plan in place to mitigate them. To document this, you might conduct an internal self-assessment, send security questionnaires to business partners, and conduct facility and management reviews. The goal is to take an objective look at your organization and gain confidence that you’re meeting MSC or, that you’ve identified areas of risk and have plans in motion to improve them.
The second part of the risk assessment is the international portion. You’ll need to identify threats that exist within a country or region based on your business model and various roles in your supply chain. This is known as a threat assessment and is meant to identify threats that are outside of your control. Examples include terrorist activity, drug smuggling, hijacking, corruption levels, and human smuggling. When assessing risk, a simple way to label each threat is:
Once the threats are assessed, you can dedicate more time and resources to the “high” areas of risk to mitigate them.
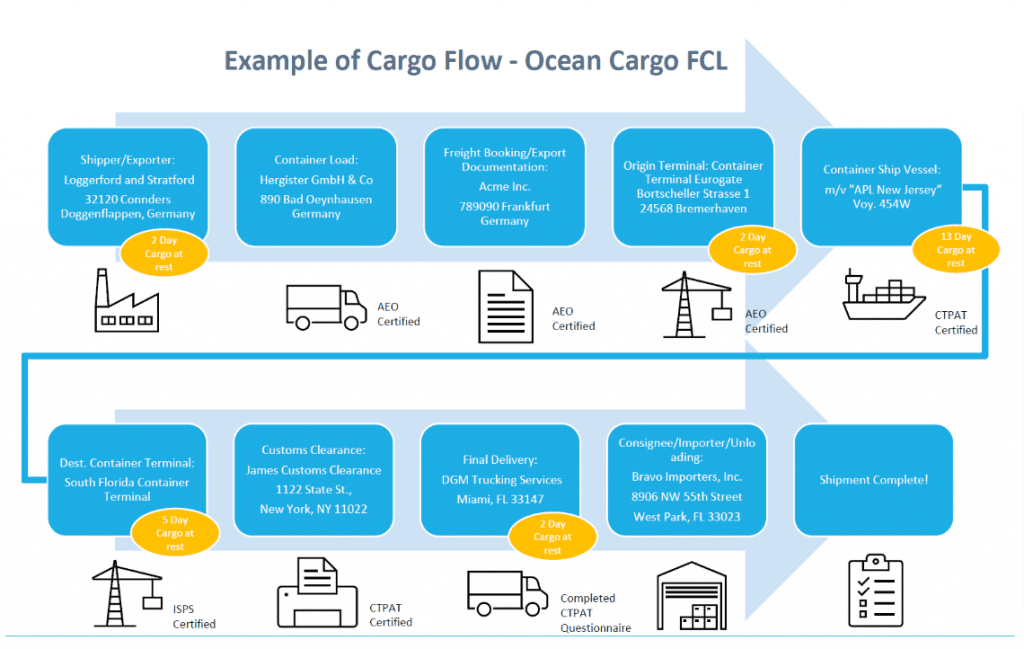
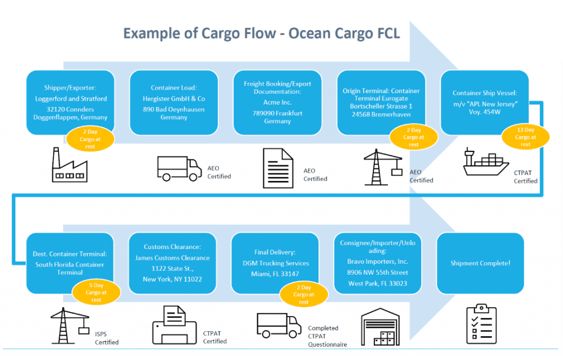
The international risk assessment also needs to contain cargo mapping, or how your cargo moves from the point of origin to the importer’s distribution center. The mapping needs to include all parties that are involved with moving cargo, whether directly or indirectly. This includes:
In addition, you’ll need to look at all transportation legs, especially when cargo is “at rest,” where it is likely more vulnerable. Here is an example of a foreign manufacturer’s cargo mapping:
If threats have been identified in your supply chain, an action plan needs to be put in place to improve them. Examples of mitigating risk include security questionnaire reviews or site visits to address vulnerabilities. It’s very important that you have a process available to create change. You need to be able to log the threat, assign an action plan to mitigate it and resolve it. Veroot’s CTPAT compliance software allows you to do just this. Store your action plan, check in on its progress, and check items off the list once they’re complete. Having a central location to store your action plan, security questionnaires, SOPs, management reviews, and more will put you at ease knowing you have all your CTPAT compliance documentation on hand.
The work doesn’t end after you’ve compiled your initial risk assessment — it needs to be completed annually. If a CTPAT member has several “high” risk factors, assessments may need to be completed more often. Examples of when this would be necessary include an increased threat level from a specific country, periods of heightened alert, changes in business partners, and/or changes in corporate structure/ownership.
The most important piece of advice when seeking CTPAT compliance is to document everything. According to the CBP, to meet the MSC for risk assessment, you must have written procedures in place that address crisis management, business continuity, security recovery plans, and business resumption. Not only is this a good practice as a company, but cataloging and writing everything down gives you the evidence you need to successfully answer the CBP when they ask about your risk assessment.
As you can see, conducting, documenting, and monitoring your risk assessment is no small feat. Many organizations that are seeking CTPAT compliance have dedicated internal resources to accomplish these tasks, but many do not. That’s where Veroot comes in. Our CTPAT compliance software simplifies the process for you — whether you are looking to become CTPAT compliant for the first time or are up for revalidation. Our software makes the risk assessment portion of your compliance easier with:
With an automated process, our customers save an average of 85% – 90% of the time they used to spend managing their CTPAT membership the old-fashioned way. In addition, we also offer CTPAT training if your team needs general ongoing education, instructional videos, or help keeping up with evolving regulations. Let’s get you CTPAT-certified — together. Get in touch with us today to get started.

In 2019, U.S. Customs and Border Protection (CBP) updated its minimum security criteria (MSC) to address changes to the global supply chain and the...

As companies continue to navigate new minimum security criteria, CTPAT Physical Security requirements are a common area of confusion – specifically...

Have you ever wondered how much trust really matters in global trade? A lot more than you think. When your business relies on partners around the...