The Ultimate Guide to Huntress EDR and Veroot Partnership for IT Providers
Veroot is a proud partner with Huntress EDR! We have complete confidence in their ability to diligently monitor our systems and collaborate with...

Anti-Virus (AV): Antivirus software, or AV, is a tool that finds and removes malware from devices. It looks for known viruses, worms, Trojans, ransomware, and other harmful software using a database of signatures.
Key characteristics of antivirus software include:
Endpoint Detection and Response (EDR): Endpoint Detection and Response (EDR) is an advanced security solution that identifies and responds to sophisticated cyber threats. Unlike antivirus, EDR focuses on broader threat detection and incident response.
Key characteristics of EDR solutions include:
In summary, antivirus software is effective at dealing with known threats, but with the increasing sophistication of cyber-attacks, it’s crucial to have a comprehensive security solution like Endpoint Detection and Response (EDR). EDR goes beyond antivirus by utilizing behavioral analysis, proactive threat hunting, and enhanced incident response capabilities to detect and respond to advanced, unknown threats.
By investing in an EDR solution, you can gain peace of mind knowing that your organization is equipped with powerful tools to safeguard against targeted attacks and advanced persistent threats. Enhance your cybersecurity defenses, protect sensitive data, and stay one step ahead of cybercriminals with the proactive threat detection and incident response capabilities offered by EDR. Don’t compromise your security—make the smart choice and secure your endpoints with EDR today.
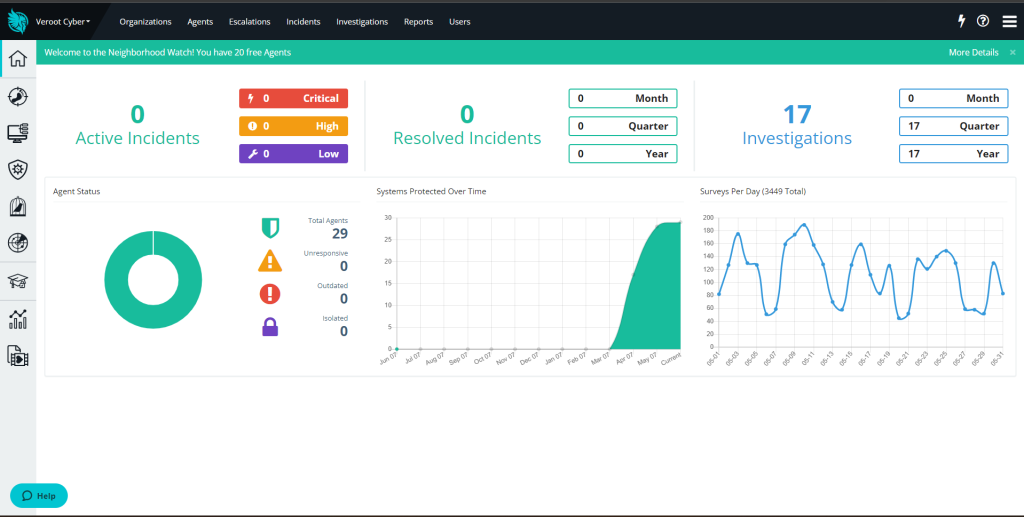
Veroot is a proud partner with Huntress EDR! We have complete confidence in their ability to diligently monitor our systems and collaborate with...
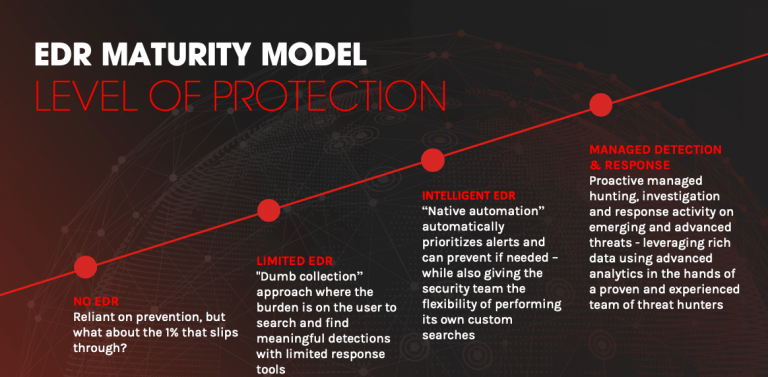
EDR is important for IACs as it helps them detect and prevent cyber threats from endpoints. With EDR, IACs can quickly identify anomalies, such as...
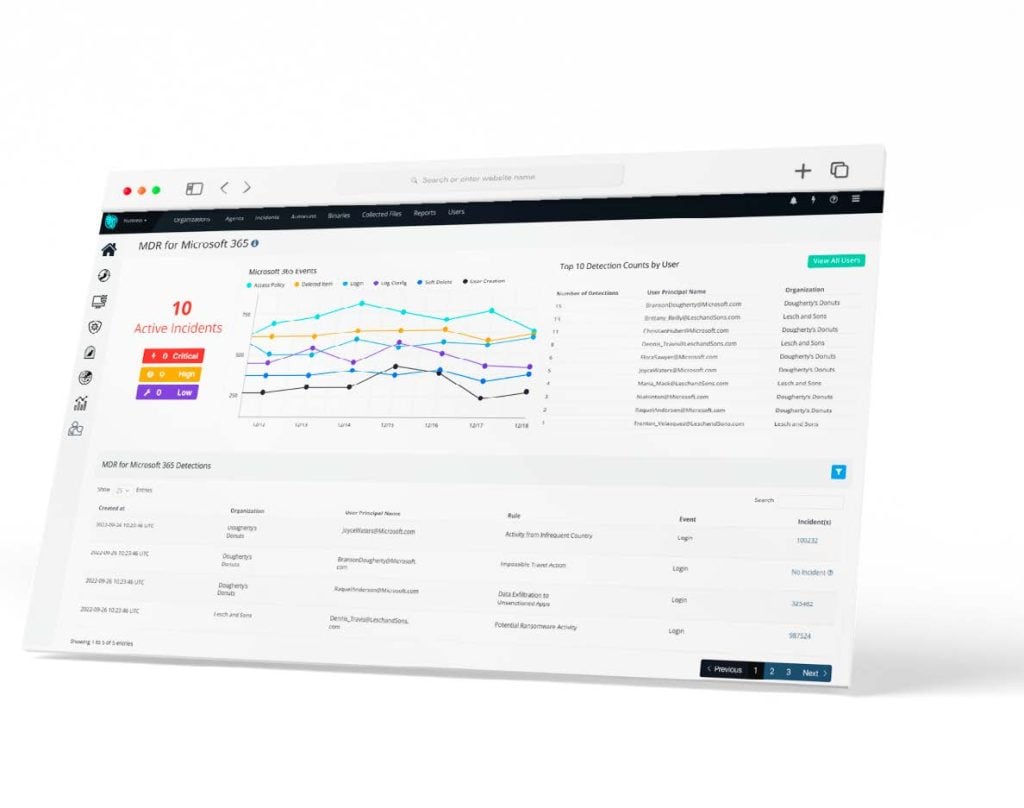
Protect Your Cloud by Stopping Cyber Attacks Earlier with Huntress. A single stolen credential or compromised account can be used to launch a...