$25.6 Million Swindled by using Deepfake Technology in Virtual Meeting
In a recent cyber security breach at a prominent multinational corporation, a finance employee fell victim to a sophisticated scam orchestrated by...
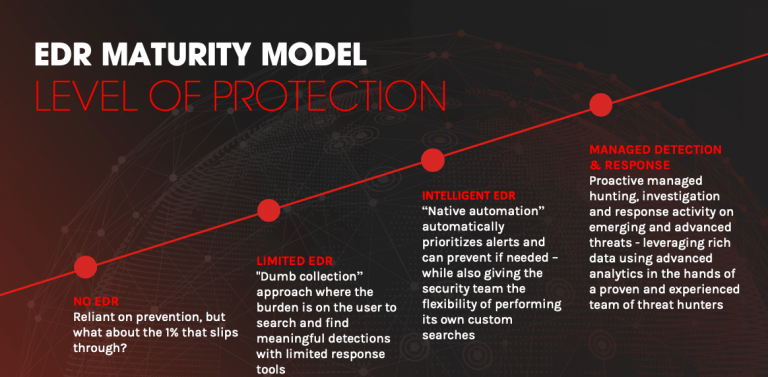
EDR is important for IACs as it helps them detect and prevent cyber threats from endpoints. With EDR, IACs can quickly identify anomalies, such as increased file transfers or unauthorized access.
EDR allows IACs to respond to new threats that anti-virus and anti-malware may miss. Cybersecurity is crucial in maintaining supply chain integrity.
EDR helps IACs protect their infrastructure and data from unauthorized access, breaches, and other threats, thus ensuring that IACs meet security objectives and follow compliance regulations.
With EDR, IACs can quickly identify anomalies in endpoint behavior, such as a sudden increase in file transfers or unauthorized access to sensitive information.
We also want to make sure that our EDR solution comes with 24/7 monitoring. This will make sure that when disaster strikes, we have a dedicated team ready to contain the breach.
EDR also allows IACs to detect and respond to new and emerging threats that may bypass traditional signature-based anti-virus and anti-malware solutions.
Furthermore, given the important role IACs play in the transportation of goods, cybersecurity is crucial in maintaining supply chain integrity.
The use of EDR can help IACs to protect their infrastructure and the data they handle from unauthorized access, breaches, and other cyber threats.

In a recent cyber security breach at a prominent multinational corporation, a finance employee fell victim to a sophisticated scam orchestrated by...
Veroot is a proud partner with Huntress EDR! We have complete confidence in their ability to diligently monitor our systems and collaborate with...
 Read More
Read More